Cybersecurity Resources
Get the latest on cybersecurity with Zyston
Insights

How Is AI Changing Cybersecurity?
AI (Artificial Intelligence) is a rapidly emerging field that has the potential to revolutionize the way we think about cybersecurity. AI-driven ...
Insights

Introducing CyberCAST Security Program Maturity Software
Introducing the New CyberCAST Security Program Maturity Software We recently announced the release of our new CyberCAST software, ushering in a new ...
Insights

The Zyston Client Program Manager Difference
Zyston Client Program Managers Provide An Elite Standard Of Service That Sets Zyston Apart From Other MSSPs Much like the cyber threat environment, ...
Insights
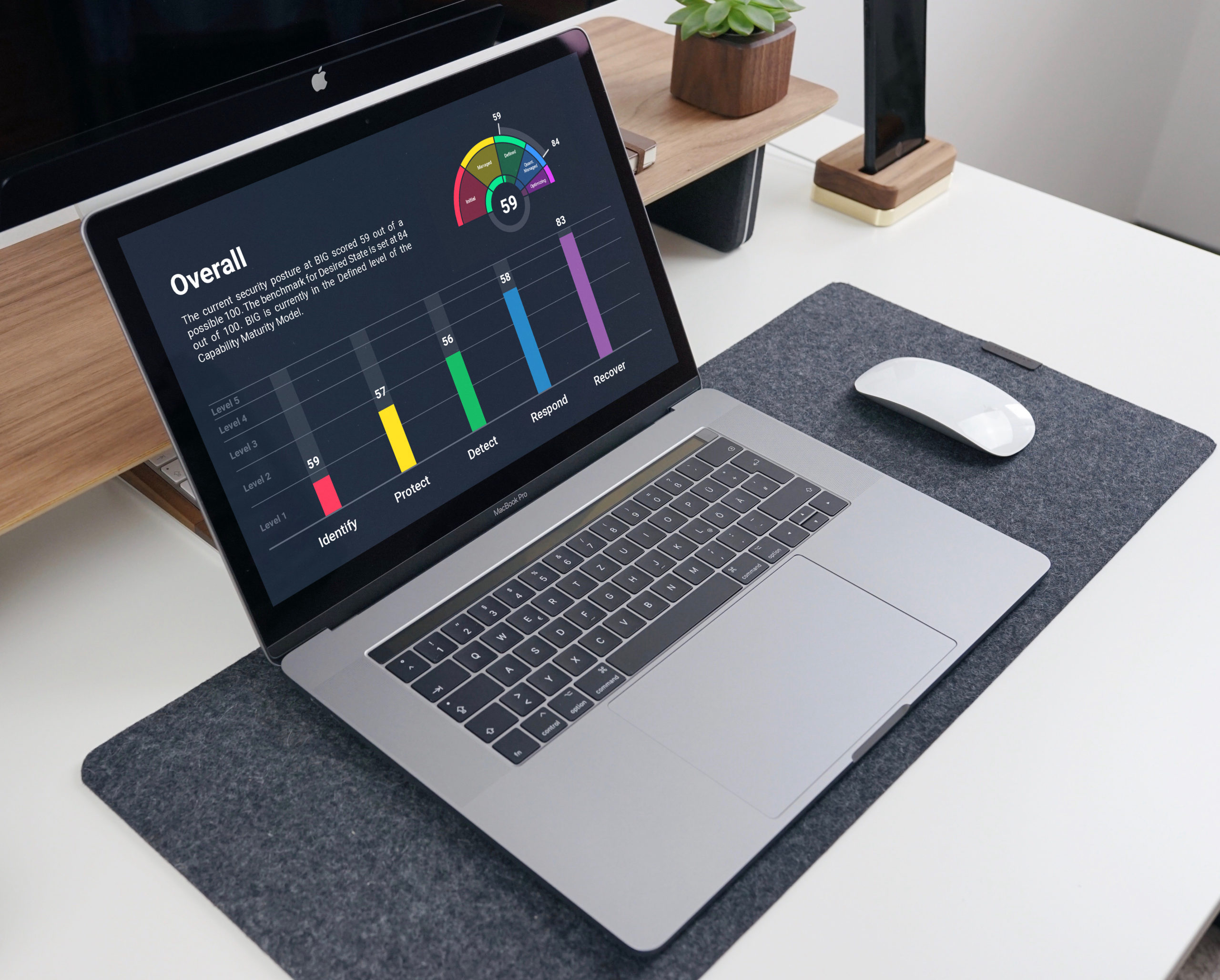
Reduce Cyberattacks In 2021 With Zyston’s New CyberCAST Security Assessment
Reduce Cyberattacks In 2021 With Zyston’s New CyberCAST Security Assessment Industry-Leading Risk Assessment Helps Companies Ward Off Widespread ...
Insights
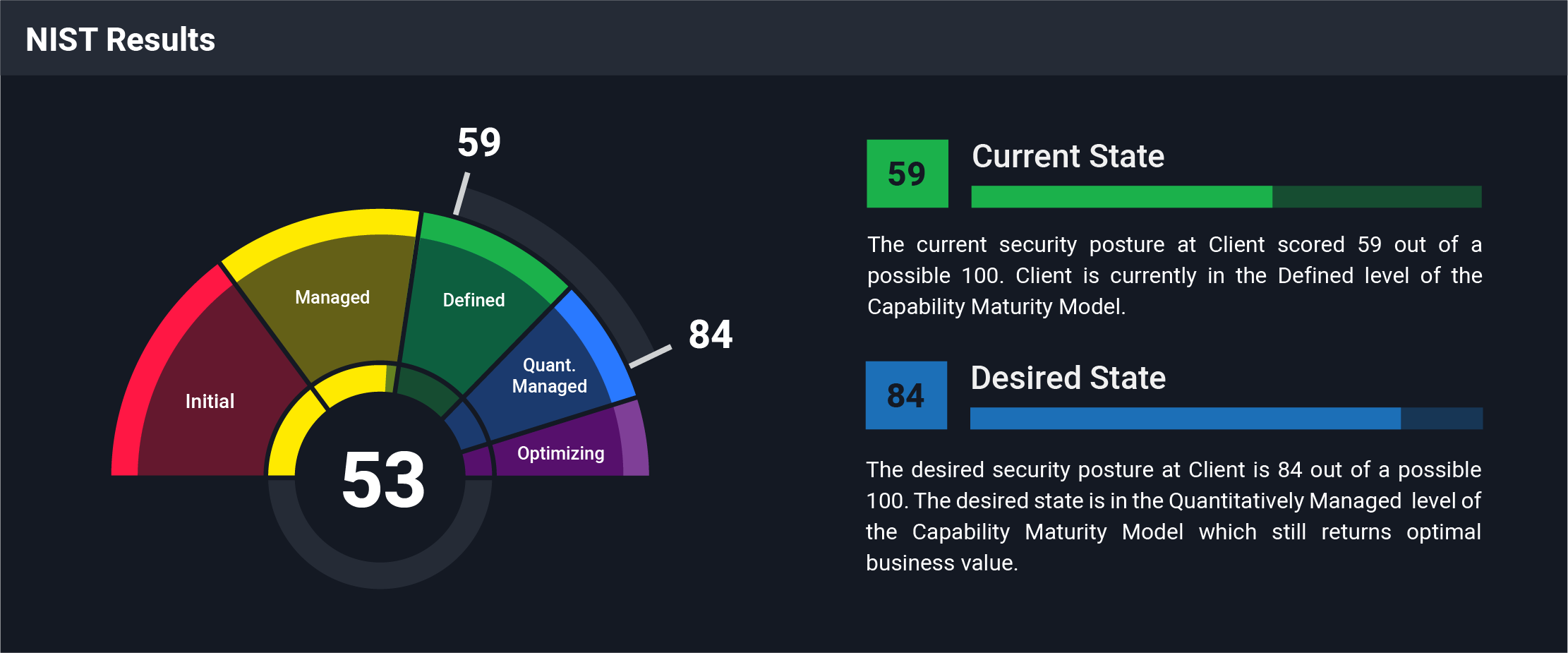
‘Zyston’ Launches ‘CyberCAST’ Cybersecurity Assessment Tool
Zyston CyberCAST – A Game Changer For Cybersecurity Industry-First Solution Evaluates Security Program Maturity And Business Risk To People, ...
Insights

Zyston Remote Workforce Monitoring
Zyston Remote Workforce Monitoring Zyston is providing a lightweight monitoring offering to monitor key assets like Office 365, VPN, and Zoom that ...
The News

Zoom Meeting Security Best Practices
Users can follow these security tips to ensure sensitive information isn’t shared with outside parties and meetings continue to run smoothly. Before ...
The News

What Is Penetration Testing in Cybersecurity?
Penetration testing, also known as pen testing, is a critical aspect of cybersecurity. It simulates real-world attacks on computer systems, networks, ...
The News

How Does Penetration Testing Work?
Penetration testing, often referred to as pen testing, is a crucial component of any organization’s cybersecurity strategy. It’s a proactive approach ...
The News

What Is the Primary Goal of Penetration Testing?
In today’s digital age, cybersecurity is a top priority for businesses of all sizes. As cyber threats evolve, businesses increasingly turn to ...
Business

How Often Should Penetration Testing Be Done
Organizations face constant threats from malicious actors seeking to exploit system vulnerabilities. Penetration testing, or pen testing, is crucial ...
Business

What Is the Difference Between Vulnerability Assessment and Penetration Testing
Staying one step ahead of potential threats is paramount. Vulnerability assessments and penetration testing are two crucial practices that ...
The News

Internal and External Penetration Testing: The Comprehensive Guide
Penetration testing, often referred to as ‘pen testing,’ is a crucial method for identifying and addressing an organization’s weaknesses, ...
The News

Sverica Capital Management Announces Growth Investment in Zyston
Sverica Capital Management Announces Growth Investment in Zyston SAN FRANCISCO, July 11, 2023 /PRNewswire/ — Sverica Capital Management LP ...
The News

Zyston Announces Complyify Acquisition
Zyston Announces Complyify Acquisition Zyston, a leading Managed Security Services Provider (MSSP) headquartered in Dallas, Texas, is thrilled to ...
The News

Zyston Announces Acquisition of Blue Lava
Zyston Announces Blue Lava Acquisition Dallas, Texas – October 5th 2023 – Zyston, a leading Managed Security Services Provider (MSSP) based in ...
The News

The Comprehensive Guide to a Cyber Security Risk Assessment Report
In today’s rapidly evolving digital landscape, businesses face an increasing number of sophisticated cyber threats. According to the National Cyber ...
The News
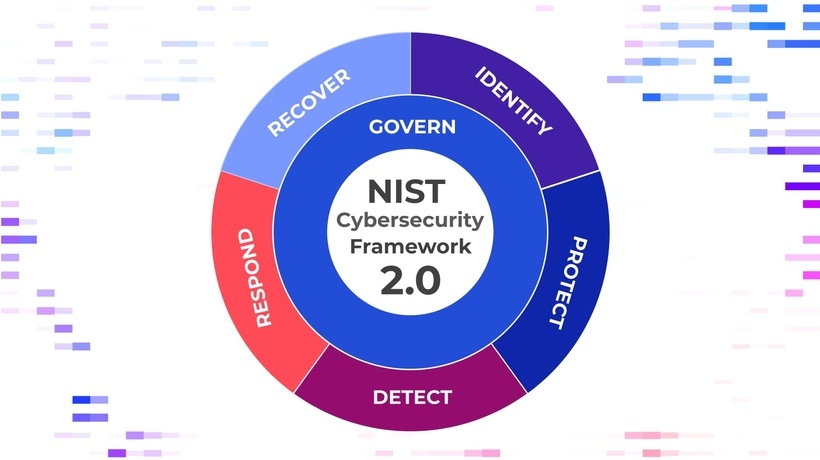
Why NIST CSF 2.0 is the Superior Framework for Measuring Cybersecurity Maturity
In today’s increasingly complex cybersecurity landscape, businesses of all sizes face a relentless barrage of cyber threats. As these threats evolve, ...
The News

Cybersecurity Risk Management: Achieving Program Maturity by Connecting Risks to Dollars
In today’s digital landscape, cybersecurity risk management has evolved from being a technical concern to becoming a critical business issue that ...
The News

Navigating the Future of Cybersecurity with Continuous Threat Exposure Management (CTEM)
In the evolving landscape of cybersecurity, one truth stands clear: threats are relentless. Cyber adversaries are continuously adapting, devising new ...
The News
Announcing CyberCAST 4.0
Author: Jeremy Powell, Chief Technology Officer Transform Your Security and Security Teams: Introducing CyberCAST 4.0—your ultimate solution for ...

